

“A well-designed network visibility fabric will help enterprises assure network and application performance and reduce security and compliance risk.”
We’ve previously explored the importance of the access layer in a well-designed network visibility fabric. So if you haven’t read that post yet, I’d suggest starting there, as the access layer truly is the foundation of your visibility fabric.
Today, we will be exploring the second layer of the network visibility fabric called the Aggregation layer and how it will be useful for increasing the usage of your security tools investment.
Building on the foundation of network TAPs at the access layer, a well-designed network visibility fabric may require an aggregation layer if the enterprise needs to monitor either a large number of network segments, or a large, distributed network. Typically comprised of 1G/10G Fiber uplinks, the Aggregation Layer allows end point devices to communicate with each other.
The actual devices comprising the aggregation layer can be Network Packet Brokers, or less full-featured devices, like Advanced Aggregators, that specialize in pushing packet flows upstream to NPBs. Aggregators are devices designed to increase efficiency and port utilization of NPBs. They collect flows from TAPs and forward them to the core of the fabric. Aggregators are also capable of pre-filtering traffic prior to sending out to NPBs for advanced filtering. They improve ROI by reducing the total cost of a network visibility fabric solution, while increasing the efficiency of existing infrastructure.
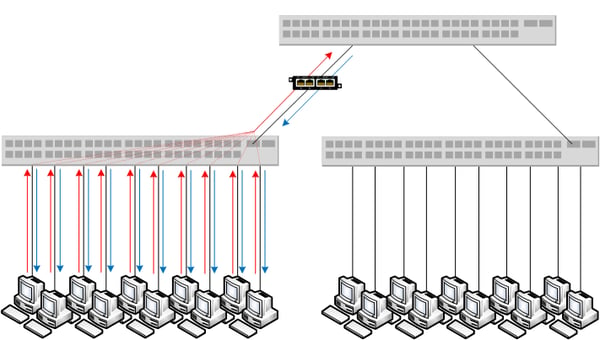
Distributed networks often have their aggregation layer devices in remote sites. These NPBs and aggregation devices will usually tunnel packet flows back to the core of the fabric, where full-featured NPBs and the analysis tools are located. In fact, EMA research has found that 35% of enterprises have NPBs deployed in remote sites, and another 30% plan to deploy them remotely by the end of 2021. By having an Aggregator pre-filter traffic before it’s sent back to the core, you can reduce the cost and payload of traffic at the core.
Very dense fabrics that are monitoring many segments of the network, will need an aggregation layer to collect traffic, perform some deduplication and other data processing, and forward the traffic to the core of the fabric. Without the aggregation device, the number of ports required on the full-featured NPB will be very high.
When your team is designing a network visibility fabric, it’s important to look at all the areas of the network where complete visibility is required to meet your business initiatives. The number of links that you want to monitor will directly affect the architectural approach you take. Taking into consideration the budget your team has to spend, you’ll quickly see the advantages of adding an aggregation layer to your design.
Looking to add an aggregation solutions to your next deployment, but not sure where to start? Join us for a brief network Design-IT consultation or demo. No obligation - it’s what we love to do!
If the inline security tool goes off-line, the TAP will bypass the tool and automatically keep the link flowing. The Bypass TAP does this by sending heartbeat packets to the inline security tool. As long as the inline security tool is on-line, the heartbeat packets will be returned to the TAP, and the link traffic will continue to flow through the inline security tool.
If the heartbeat packets are not returned to the TAP (indicating that the inline security tool has gone off-line), the TAP will automatically 'bypass' the inline security tool and keep the link traffic flowing. The TAP also removes the heartbeat packets before sending the network traffic back onto the critical link.
While the TAP is in bypass mode, it continues to send heartbeat packets out to the inline security tool so that once the tool is back on-line, it will begin returning the heartbeat packets back to the TAP indicating that the tool is ready to go back to work. The TAP will then direct the network traffic back through the inline security tool along with the heartbeat packets placing the tool back inline.
Some of you may have noticed a flaw in the logic behind this solution! You say, “What if the TAP should fail because it is also in-line? Then the link will also fail!” The TAP would now be considered a point of failure. That is a good catch – but in our blog on Bypass vs. Failsafe, I explained that if a TAP were to fail or lose power, it must provide failsafe protection to the link it is attached to. So our network TAP will go into Failsafe mode keeping the link flowing.
Single point of failure: a risk to an IT network if one part of the system brings down a larger part of the entire system.
Heartbeat packet: a soft detection technology that monitors the health of inline appliances. Read the heartbeat packet blog here.
Critical link: the connection between two or more network devices or appliances that if the connection fails then the network is disrupted.