
Sole reliance on SPAN ports for network visibility and monitoring has been on the decline for years. IT teams have realized the inherent limitations of SPAN ports and have shifted towards the traditional 3-tiered approach to network visibility, Physical Layer TAPs, Network Packet Brokers, and Tools.
Tier 1: Physical Layer TAPs
Network Test Access Points (TAPs) are hardware tools that allow you to access and duplicate network traffic. TAPs supply full line rate traffic and are never oversubscribed or rate limited. In the traditional 2-tier approach, the egress traffic from the TAPs is sent directly to NPBs.
Tier 2: Network Packet Brokers
Network Packet Brokers (NPBs) are responsible for efficiently funneling data from network TAPs and SPAN ports to each tool. NPB’s were originally designed to replicate traffic for multiple tools while reducing the volume of traffic to each tool, ensuring each tool operates as efficiently as possible. This is typically done through a combination of aggregation, replication and L2-L4 filtering. The groomed, tool specific traffic is sent out for processing.
>> Download Now: Aggregation - Adding Value Back Into Your Network and Maximise ROI [Free whitepaper]
Tier 3: Tools
Tools are responsible for processing and characterizing traffic of interest. Common tools are built for application performance monitoring, security, and data forensics.
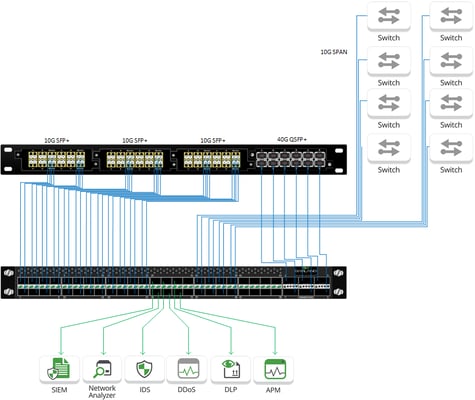
3-Tiered Visibility Fabric
This approach has provided, and continues to provide, pervasive network visibility. So why do we see the approach to network visibility fabrics changing? This 3-tiered approach was originally intended to increase the efficiency of monitoring and security tools. Tools continue to be the most significant cost associated with network monitoring and are continually evolving to be more capable. This has driven the evolution of the NPBs to be extremely complex devices. NPBs now offer advanced features including L2-L7 filtering/classification, deduplication, metadata generation, and SSL/TLS decryption. With the well documented explosion of data, the NPB cost per port should have rapidly declined. The price has come down, but the reduction is not proportional to the increased number of ports needed to monitor growing networks. This leads to either ballooning budgets for security and monitoring, or an increase in blind spots within the network.
The increase in data and complexity of NPBs have pushed the market towards a 4-tiered approach. This brings the rise of the aggregation layer.
New Approach: Aggregation Layer
Tier 1: TAPs
Tier 2: Aggregation – Aggregators are devices designed to increase efficiency and port utilization of NPBs. Considering the NPB cost per port, can we justify a direct connection with 60% utilization? In some cases, maybe, but the justification gets more difficult as we move towards the edge where it is common to see utilizations <5%. Aggregators condense multiple streams of low utilization links down to as few as one or two ports on the NPB. Aggregators also capable of pre-filtering traffic prior to sending out to NPB’s for advanced filtering.
Tier 3: NPBs
Tier 4: Tools
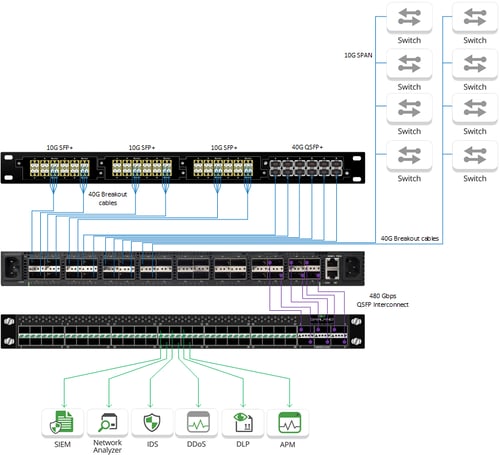
Figure 2. 4-Tiered Visibility Fabric
Aggregators improve ROI by reducing the cost of network visibility. Whether it’s a new install or an upgrade of existing infrastructure the addition of Aggregators leads to a more efficient use of costly NPBs. Take a simplified example: If your current NPB has 50% utilization on all ports, adding an aggregator can potentially free up half of your NPB ports. This pushes out the time to purchase new NPBs or allows you to now monitor parts of your network that may have previously been neglected. A purpose-built Aggregator should not exceed $1k/100G interface, making it 50-75% less expensive than a full-featured NPB. With the cost savings and improved efficiency, it’s easy to see why most networks have shifted, or will shift, to this 4-tiered approach.
Important considerations when purchasing an Aggregator:
- Support for multiple speeds and media types, including Cisco 40G/100G BiDi
- High density 1U form factor
- Selective aggregation based L2-L4 criteria
- N:1, 1:N, and N:N port mapping
- Remote management options
- COST
Looking to add an aggregation solutions to your next deployment, but not sure where to start? Join us for a brief network Design-IT consultation or demo. No obligation - it’s what we love to do!

