
Supervisory control and data acquisition systems (SCADA), or industrial control systems (ICS), have been monitoring and controlling our industrial, power and refinery world since the 1960s.
Simply put, SCADA is the least protected and misunderstood technology in use. I want to highlight its challenges and go over the ways you can overcome it to protect your Industrial network.
A Brief Overview of SCADA
Early in my career I worked for a SCADA research and monitoring company, where I designed and tested production tools for the oil industry—from acquisition to refinement requirements.
SCADA started out as pure analog, focused on monitoring physical qualities, such as pressure, temperature, viscosity, voltage levels, liquid flow, wind/air speed, and salinity. SCADA systems typically operated as an independent system, telling human operators if the system they were monitoring was working within correct parameters. Later, the systems reported back to computers that calculated if everything was okay; if not, it made the decision to either change parameters or shut down systems that were in danger.
For the majority of these years, SCADA and ICS systems were completely independent, and each had a different human interface, reporting programs/methods, communications methods, languages, alert/failure alarm systems, and methods. Today, Ethernet and the internet are becoming part of the industrial system operation and a sub-assembly of the Internet of Things (IoT).
Ethernet Introduces Greater SCADA Vulnerabilities
Ethernet brings interoperability, bandwidth efficiency, and finer granularity, which result in greater savings or earnings depending on your organization’s goals. Of course, the industrial machine now also faces the same vulnerabilities from the cyber world as the rest of us—an IP doorway in.
Once an IP address is identified, these systems—including sensors, controls, and human machine interface displays (HMI)—are relatively easy to hack. This scenario is no longer speculation or Hollywood movie plots, as several attacks have been publically documented; SCADA attacks started as far back as the 1980s, with the first being the Farewell Dossier.
Since then, here are the documented attacks:
- Slammer early 2000
- SoBig early 2000
- Sasser 2004
- Conficter
- Night Dragon and Stuxnet 2009
- Havex RAT and Blacken
- Black Energy 2014
- Ukraine Power Grid 2015
>> Download now: Learn how to secure your industrial network
[Free Whitepaper]
SCADA Vulnerabilities Are Only Just Beginning
What is more frightening are the compromised systems that have yet to be discovered. There are thousands of SCADA system worldwide, and they control everything we touch and experience in our environment: water, sewage, natural gas, gasoline, electrical power, food production, flood control, dams, pharmaceuticals, refineries, weapons, bombs, airplane production and control, transportation, fire and explosion control, etc.
One of the most powerful attack packages is Agora SCADA+ Exploit pack from GLEG, a Russian security firm. This infamous package consisted of 22 exploits and 11 zero-day vulnerabilities, along with many details on SCADA/ICS issues that allow access attacks (such as hardcoded passwords and many other known weak areas).
A 2014 research project, called SHINE (SHodan INtelligence Extraction), located SCADA/ICS devices that were, in some way, connected to the Internet. The researchers’ reported locating over 2.2 million unique devices. Of the sampled devices, 586,997 were industrial systems with IP addresses that belonged to SCADA /ICS control systems, and others were related to software technologies.
This research project was run by top internet researchers Bob Radvanovsky and Jake Brodsky from Infracritical. These 1+ million SCADA/ICS access points are all a vulnerability and a high-security risk, and must be addressed, as they should be considered an international emergency.
Visibility—The Solution to SCADA Threats
 The solution is visibility from the traditional Ethernet arena to the PC104 command and control network. The PC104 is the interconnect standard for embedded industrial technology, and this network TAP is the top of stack visibility plane. A TAP has the only Ethernet access capability, and allows visibility into the control and monitoring world.
The solution is visibility from the traditional Ethernet arena to the PC104 command and control network. The PC104 is the interconnect standard for embedded industrial technology, and this network TAP is the top of stack visibility plane. A TAP has the only Ethernet access capability, and allows visibility into the control and monitoring world.
The other boards are the access to the RTU (remote terminal unit), meaning they interpret what is being monitored (for example, heat/temperature, pressure, flow, etc). Here the processors in the stack interpret the RTU’s report and take action, which could be in the form of either alerts or reports. By being able to monitor the interconnect via Ethernet, we will have visibility and will know about attacks or failures.
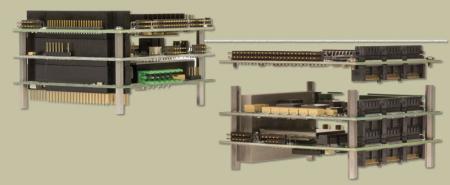
Another critical element to the PC104 stack is the casing, which is designed specifically for the industrial environment (in a previous post I listed these requirements). With PC104, the hardened case prevents environmental elements from causing a failure.
The need to protect our control technology are just beginning to be seen. As we rely more on the IoT, industrial networks need to put safeguards in place.

