
Network connectivity is critical to any security or network monitoring project. Many are always asking us which network TAP is right for them. In a recent post, we discussed the ins and outs of passive network TAPs which are typically paired with out-of-band monitoring solutions.
Today, we’ll take an in-depth look at active network TAPs and see where, when and how they fit into a complete visibility strategy.
Active Taps are Necessary When any One of the Following Conditions are Present:
- An inline security appliance is being deployed such as an IPS or firewall. In this case the active TAP is classified as a Bypass TAP.
- A copper Gigabit segment is being monitored. Gigabit copper is a special case that requires the two endpoints being monitored to link to the TAP, regardless of the application.
- A monitoring tool will be used that injects packets into the network, such as TCP Reset Packets.
What is an Active Network TAP?
Garland defines an active network TAP as a TAP that is physically linked to the monitored devices. If the power is lost on the TAP Garland has proprietary failsafe circuitry that connects the two monitored devices together so traffic continues to flow.
Active TAPs require power to support additional functionality like aggregation and regeneration as well as advanced functions like filtering and bypass.
The whole point of deploying network TAPs of any kind is to ensure total visibility for any connected appliances. These purpose-built devices are inserted directly into the network to provide complete access to traffic data at the source. Unlike switch SPAN ports or other secondary sources that can be overwhelmed during traffic spikes, network TAPs pass 100% of the bits, bytes and packets that they see directly to the connected security appliances or network monitoring tools.
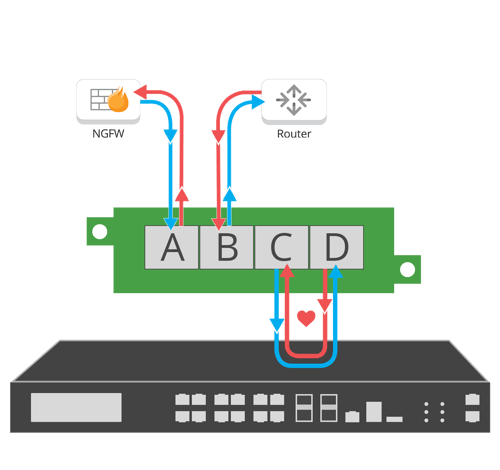 Diagram 1: Active TAP in Bypass Mode
Diagram 1: Active TAP in Bypass Mode
Active network TAPs are frequently designed to support inline security applications, such as firewalls, anti-malware devices, intrusion protection systems and more. These security systems are unique because they take in traffic from the outside world and attempt to block suspicious communications from getting inside the company. Naturally, these appliances require a TAP that can feed them network traffic without losing packets – but they also need a solution able to accept the authorized traffic as well as messages from the appliance and let them travel to their intended destination. Only an active network TAP can facilitate this type of communication.
Download Now: Network TAPs 101 - The Networking User Guide [Free eBook]
Providing Inline Security Device 100% of the Packets
The biggest reason companies use active TAPs is to ensure that their key front-line security systems don’t miss packets, a risk that most CSOs prefer to avoid. However, this deployment method offers another key benefit – security appliances can easily be moved to an out-of-band status in the event that the company needs to troubleshoot issues or make updates. If firewalls and other appliances must remain in-line during the upgrade process, there is a good chance that normal traffic flows will be disrupted and cause issues for other applications. Taking firewalls out-of-band for a few minutes is the fastest way to see if a persistent issue originates with the network or the security system.
Simply put, active TAPs make life easier for the people tasked with managing today’s complex IT environments. And, the firewall still sees 100% of the network traffic while it is running out-of-band so the risk to the organization is minimal.
Providing Network Access in Copper Gigabit Environments
Organizations looking to provide connectivity for security or network monitoring devices in high speed copper environments must use an active network TAP regardless of whether or not the appliance is inline or out-of-band. Passive TAPs cannot be deployed in copper gigabit environments because of the way that data is simultaneously transmitted and received over the copper pairs – the endpoints don’t get a clear picture of what is coming and what is going.
Ensuring Effectiveness
Unlike certain passive TAPs, all active network TAPs require power to function. That means that you need a failsafe mechanism to ensure that you haven’t introduced a possible failure point into the network. All Garland active TAPs were designed to recognize power outages and automatically close the relay circuitry in less than 8 milliseconds providing a passive connection between your two network elements.This ensures network uptime while your network administrators figure out the power loss issue.
While all network TAPs serve the same need – ensuring that connected devices receive 100% of the traffic data they require to their job – you need to pick the one that best suits your application and environment.
Looking to add an active TAP to your next deployment, but not sure where to start? Join us for a brief network Design-IT consultation or demo. No obligation - it’s what we love to do!

