
You just bought a brand new inline security appliance—a next-gen firewall, intrusion prevention system (IPS), data leakage prevention (DLP) system or web application firewall—and you’re ready to deploy it in your network. But then it sits in a box for months because you look at the network design and can’t decide where the new appliance will fit in.
The whole point of an inline security appliance is to actively analyze every bit, byte and packet® you send to it—let’s go over the keys to connecting your new inline security appliance for optimal network access.
One Big Mistake to Avoid: Connecting The Appliance to the Live Network
If you want your security appliance to actively analyze network traffic, your first thought might be to place it right between the two network elements you want to monitor traffic for (for example, a router and switch). Resist this thought. The design would look like this:
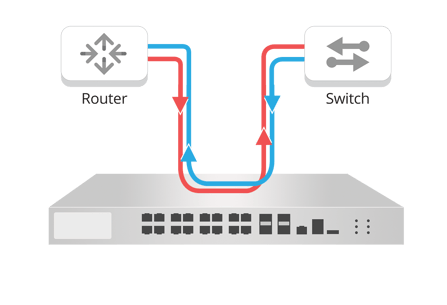 Under ideal conditions, this design might seem effective—but it will cause major issues in your network, including:
Under ideal conditions, this design might seem effective—but it will cause major issues in your network, including:
- Introducing a point of failure in the event of a power outage or if a link goes down
- Traffic manipulation that causes frame misalignment
- Performance delays throughout the network
- Dropped packets that make the security appliance ineffective
A Common Misconception: Connecting with a SPAN/Mirror Port
We often discuss why SPAN ports are no longer an effective means of ensuring network visibility, but many customers still use them extensively. SPAN ports may have been effective enough when we were only analyzing 10Mbps links, but now they introduce a number of issues, including:
- Oversubscribed ports
- Dropped packets
- Limited scalability as network speeds increase
- Negative effect on packet timing
- SPAN ports become a point of failure when links go down
These are only a few of the problems that SPAN ports introduce when they are used as network TAP replacements. That’s why network TAPs are the best practice for in-band security appliance connectivity.
>> Download now: Learn how to improve your IT security with better threat detection and prevention tool deployment.
Network TAPs – A Best Practice by Industry Leaders
 What do Palo Alto Networks and Cisco all have in common? They partner with Garland Technology as their network TAP vendor.
What do Palo Alto Networks and Cisco all have in common? They partner with Garland Technology as their network TAP vendor.
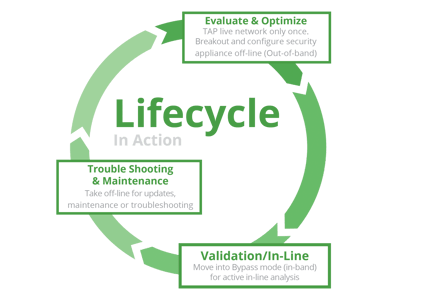
When you need to ensure 100% uptime and visibility for inline security appliances, a bypass network TAP is the only option.
With a bypass TAP you can configure and validate your inline security appliance off line. Once fully validated, you can be deploy them inline for active analysis. Another key feature is the ability to take the security appliance back off-line without interrupting network traffic for updates, maintenance or troubleshooting.
Network bypass TAPs have a variety of features—the key is to find the solution that meets your needs today and is scalable for tomorrow.
Key Considerations when Choosing a Bypass Network TAP
Bypass TAPs are not a one-size-fits-all solution. When purchasing a bypass TAP for your network, consider the following:
- Cable and media conversion: Copper or fiber network and monitoring ports? Do you need to convert TX to LX? Or LR to ER?
- Scalability: How many security appliances do you need to TAP today…and tomorrow?
- Network Speed: 1G/10G/40G/100G
Deploying a Bypass Network TAP
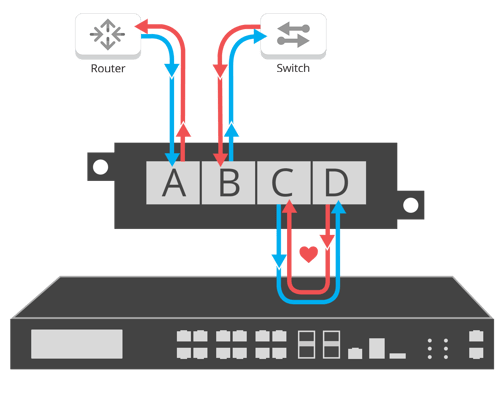
Bypass network TAPs are placed between the inline appliance and the router/switch links that they are taking traffic from. The router and the switch are plugged into Network Ports A and B and the inline appliance is plugged into Monitor Ports C and D, giving total visibility without introducing a point of failure. See the following graphic for an example:
Quick Connection Requires Pre-Planning
Network TAPs aren’t one-size-fits-all solutions. If you want to ensure optimal network access for your new inline security appliance, you must understand your network specifications and purchase the appropriate bypass TAP.
Looking to add IT Security solution to your security deployment, but not sure where to start? Join us for a brief network Design-IT consultation or demo. No obligation - it’s what we love to do!

