
If you read enough articles about the evolution of industrial networks, you might think the Industrial Internet of Things (IIoT) is set to take over the world. And while it’s important to plan ahead for the significant changes that IIoT will require, let’s not get ahead of ourselves.
Industrial Ethernet connectivity is a requirement to unlock the benefits of IIoT. We’ve discussed the rise of Industrial Ethernet on multiple occasions, but it may not be as widely adopted as you’d expect.
In 2017, HMS found that Industrial Ethernet (46%) and wireless (6%) only accounted for 52% of total industrial connectivity. While they’re growing at rates of 22% and 32%, respectively, that still leaves 48% of industrial networks with traditional fieldbus networks.
Fieldbus networks and legacy equipment have their advantages, but increasing demands to bridge IT capabilities and OT processes cause problems with maintaining them.
Fieldbus vs. Ethernet in the Industrial Network
One key difference between fieldbus networks and Ethernet is that the former is deterministic and the latter is collision-based. How does this shift impact your industrial network?
Legacy equipment persists for decades because of its superior abilities to maintain the safety and security of critical infrastructure. Since the 1990s, something like PROFIBUS has been able to keep modular, private connections between industrial devices running safely. Your fieldbus systems were purpose-built for the rigor of industrial environments—connections are rugged, speeds are slower, and bandwidth requirements are low.
With so many modular fieldbus systems throughout a plant floor, it’s difficult (sometimes seemingly impossible) to migrate to new equipment. The risk of shutting down multiple processes and disrupting the network is just too high. That’s why we see so many industrial networks running old versions of Windows 95 and pushing equipment to the limits of support periods.
>> Download now: Learn how to secure your industrial network
[Free Whitepaper]
Industrial Ethernet, on the other hand, takes advantage of higher speeds to support collision-based networking. In the past, this was in stark contrast with the high reliability of fieldbus networks. Ethernet couldn’t support real-time communication or deterministic processes. The collisions that make IT applications work could (would) have severe consequences in an industrial setting.
However, non-deterministic Ethernet has evolved to support Fast Ethernet and Full-Duplex Switched Ethernet, making it a real option for your industrial network. Now, you have Industrial Ethernet that is faster, more flexible, higher bandwidth, easier to manage, and far more interoperable than fieldbus. Why, then, does fieldbus and other legacy equipment persist?
The reality is that fieldbuses and Industrial Ethernet will likely live side by side for years to come. There are devices that either don’t support Ethernet or simply don’t need it, meaning your fieldbuses will play a critical role in your IIoT future.
That’s where the problem lies. As IT and OT continue to merge, how can you make legacy equipment like fieldbuses integrate into the overall network securely and reliably?

Passive, Listen-Only TAPs Bring Legacy into Industrial Ethernet
The first challenge to overcome is getting legacy equipment to connect to the larger network at all. And with advancements in communication protocols, that is getting easier and easier.
However, the second challenge is often much harder. Your legacy equipment wasn’t designed to communicate beyond its isolated system. When you start to push legacy equipment to transfer data outside of these proprietary systems, you open the industrial network to security vulnerabilities.
The need for passive, real-time monitoring is stronger than ever in an Industrial Ethernet environment saddled with legacy equipment. And the only way to safely achieve the proper level of monitoring is with passive, listen-only network TAPs.
At Garland, we offer “no injection” aggregation network TAPs for 10/100/1000M copper networks. These will help you create unidirectional monitoring solutions that capture every bit, byte, and packet® and ensure copied packets don’t go back in and disrupt the industrial network—all in a package that’s purpose-built and unhackable.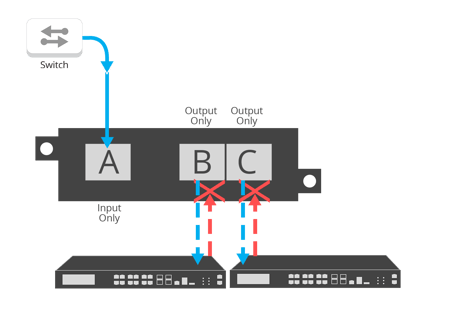
If you want to learn more about bridging the gap between your legacy equipment and the shift to Industrial Ethernet and IIoT, we’d love to help. Contact us today for more information about the importance of passive, listen-only network TAPs.
