

Garland Technology's PacketMAX™ Advanced Aggregators are very popular with customers that have a lot of tapped network links or a lot of tools to distribute monitor traffic to. In large environments, multiple aggregators may be needed to consolidate the tapped traffic down to a manageable number of monitor links for tools. While the Advanced Aggregators have web-based management consoles, customers are often looking for a way to simplify the management of these devices, especially when multiple devices are in place.
There are two approaches to simplifying this management process: creating a single-pane -of-glass centralized management platform, or making use of built-in Application Programming Interfaces or APIs.
With a centralized management platform, a dedicated web console will be used to connect into multiple devices at once, allowing the individual devices to be managed from one location. This will save time and reduce complexity in comparison to requiring administrators to log into each separate device to make changes. On the other hand, this does require customers to learn a completely new management system in addition to the other management systems their other tools are already using.
An API takes the features and capabilities of the Advanced Aggregator and makes them easily referenceable to developers that want to make use of them without having to learn and utilize the direct commands of the appliance's OS.
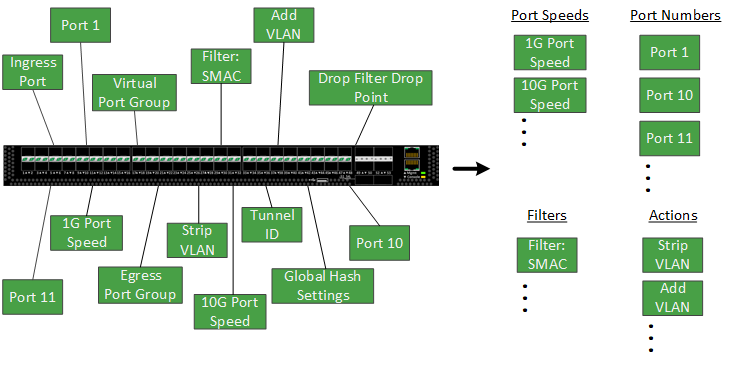
For API applications, the Advanced Aggregators use GraphQL. When a developer needs to remotely control one of the Advanced Aggregators, they'll be able to grab calls from multiple different features and organize them into a single command.
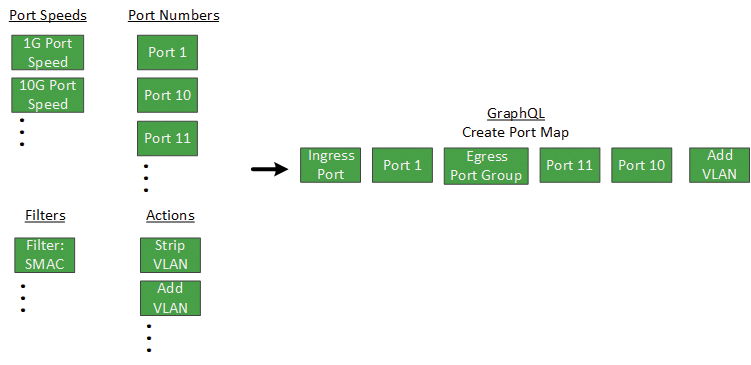
A benefit to using APIs is that you could potentially make use of a monitoring tool's existing centralized management platform to also manage the Advanced Aggregators. This could allow port maps and filters to be setup on multiple appliances without having to manually access or navigate through the Aggregator's web GUI.
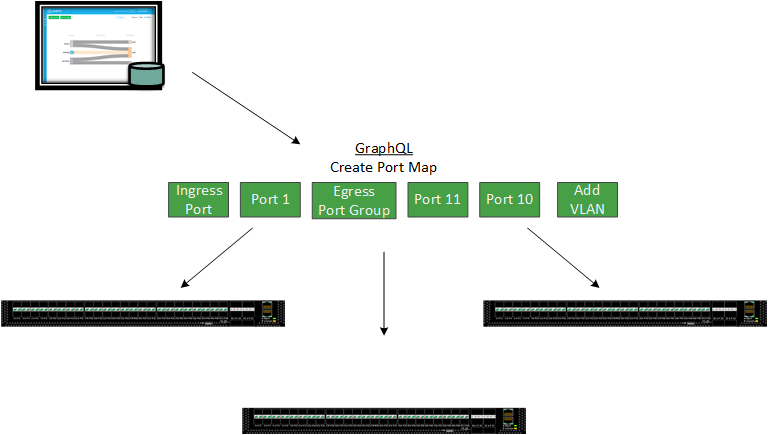
For most use cases, the Advanced Aggregator will be a set-it-and-forget-it type of appliance. In these situations, the need to update or change port maps or filters will come from a change or the implementation of new tools. If this is the case, having the control to create exactly what you need on the Advanced Aggregator from the existing tool's web console would be far more beneficial than a dedicated centralized management console or using local management.
[Want to learn more about the role of Advanced Aggregators in your network? Download the EMA whitepaper: Best Practices for Building a Network Visibility Fabric]
If the inline security tool goes off-line, the TAP will bypass the tool and automatically keep the link flowing. The Bypass TAP does this by sending heartbeat packets to the inline security tool. As long as the inline security tool is on-line, the heartbeat packets will be returned to the TAP, and the link traffic will continue to flow through the inline security tool.
If the heartbeat packets are not returned to the TAP (indicating that the inline security tool has gone off-line), the TAP will automatically 'bypass' the inline security tool and keep the link traffic flowing. The TAP also removes the heartbeat packets before sending the network traffic back onto the critical link.
While the TAP is in bypass mode, it continues to send heartbeat packets out to the inline security tool so that once the tool is back on-line, it will begin returning the heartbeat packets back to the TAP indicating that the tool is ready to go back to work. The TAP will then direct the network traffic back through the inline security tool along with the heartbeat packets placing the tool back inline.
Some of you may have noticed a flaw in the logic behind this solution! You say, “What if the TAP should fail because it is also in-line? Then the link will also fail!” The TAP would now be considered a point of failure. That is a good catch – but in our blog on Bypass vs. Failsafe, I explained that if a TAP were to fail or lose power, it must provide failsafe protection to the link it is attached to. So our network TAP will go into Failsafe mode keeping the link flowing.
Single point of failure: a risk to an IT network if one part of the system brings down a larger part of the entire system.
Heartbeat packet: a soft detection technology that monitors the health of inline appliances. Read the heartbeat packet blog here.
Critical link: the connection between two or more network devices or appliances that if the connection fails then the network is disrupted.