
August 17, 2017

We recently formalized a technology partnership with Savvius, a company I’ve been working with since early in my career when they were called WildPackets. The Savvius and Garland Technology partnership adds value to companies deploying the Savvius Omnipeek, Spotlight or Omnipliance APM/NPM solutions.
In today’s enterprise networks and data centers, IT professionals need visibility and access to the data anytime, from anywhere to perform real-time monitoring and analysis of application and network behavior. As well as the often overlooked scenario - delayed analysis.
Let’s dive into the new Savvius and Garland joint solution, case study and learn more about our upcoming webinar.
With the Garland + Savvius pre-certified deployment solution, enterprise and data center architects are assured the APM/NPM solution they are deploying has:
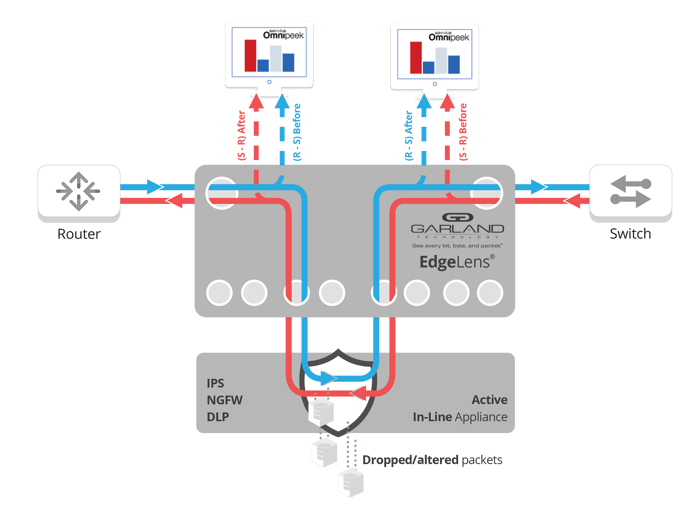
EdgeLens®, Garland’s hybrid bypass TAP with packet broker functionality provides visibility for a hybrid configuration of an active, in-line network device and off-line or “out-of-band” tools, such as Savvius. EdgeLens provides identical network traffic streams through the active in-line device and to the capture engine of Savvius Spotlight or Omnipeek monitoring and analysis applications.
The Garland + Savvius pre-certified solution was recently deployed to provide real time tracking and analysis of big data to IT Forensics, that included packet captures permissible for legal evidence in criminal trials.
The Garland + Savvius Solution Ensures:
With the spine leaf architecture and increased virtualization in the data center/private cloud, network architects and CIOs are challenged with how to scale the visibility cost effectively. In this webinar, Chris Bihary, CEO of Garland Technology and Nadeem Zahid, Head of Strategy/BusDev at Savvius, will discuss:
Watch the recorded webinar on our Savvius Technology partner page.
If the inline security tool goes off-line, the TAP will bypass the tool and automatically keep the link flowing. The Bypass TAP does this by sending heartbeat packets to the inline security tool. As long as the inline security tool is on-line, the heartbeat packets will be returned to the TAP, and the link traffic will continue to flow through the inline security tool.
If the heartbeat packets are not returned to the TAP (indicating that the inline security tool has gone off-line), the TAP will automatically 'bypass' the inline security tool and keep the link traffic flowing. The TAP also removes the heartbeat packets before sending the network traffic back onto the critical link.
While the TAP is in bypass mode, it continues to send heartbeat packets out to the inline security tool so that once the tool is back on-line, it will begin returning the heartbeat packets back to the TAP indicating that the tool is ready to go back to work. The TAP will then direct the network traffic back through the inline security tool along with the heartbeat packets placing the tool back inline.
Some of you may have noticed a flaw in the logic behind this solution! You say, “What if the TAP should fail because it is also in-line? Then the link will also fail!” The TAP would now be considered a point of failure. That is a good catch – but in our blog on Bypass vs. Failsafe, I explained that if a TAP were to fail or lose power, it must provide failsafe protection to the link it is attached to. So our network TAP will go into Failsafe mode keeping the link flowing.
Single point of failure: a risk to an IT network if one part of the system brings down a larger part of the entire system.
Heartbeat packet: a soft detection technology that monitors the health of inline appliances. Read the heartbeat packet blog here.
Critical link: the connection between two or more network devices or appliances that if the connection fails then the network is disrupted.