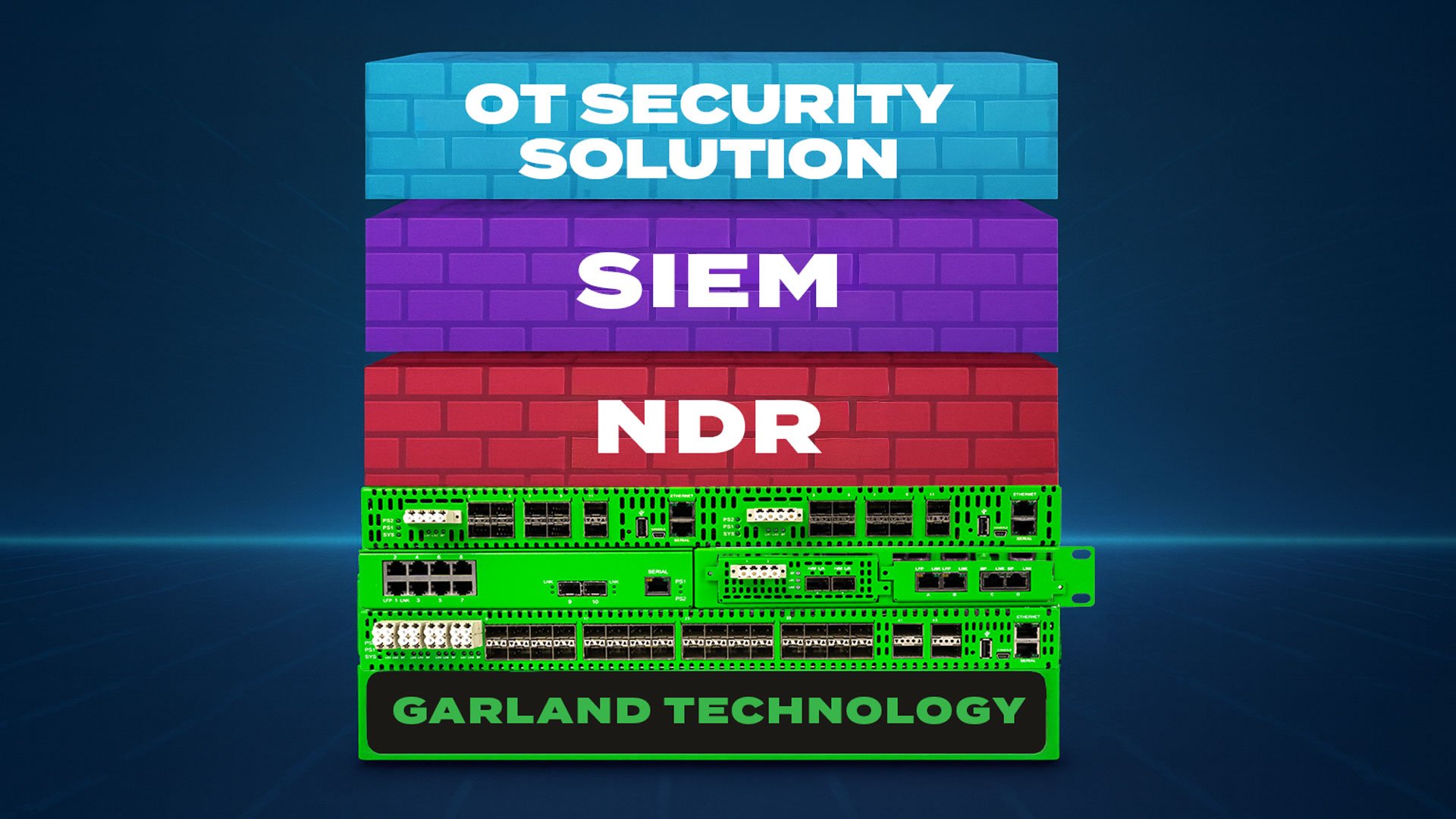
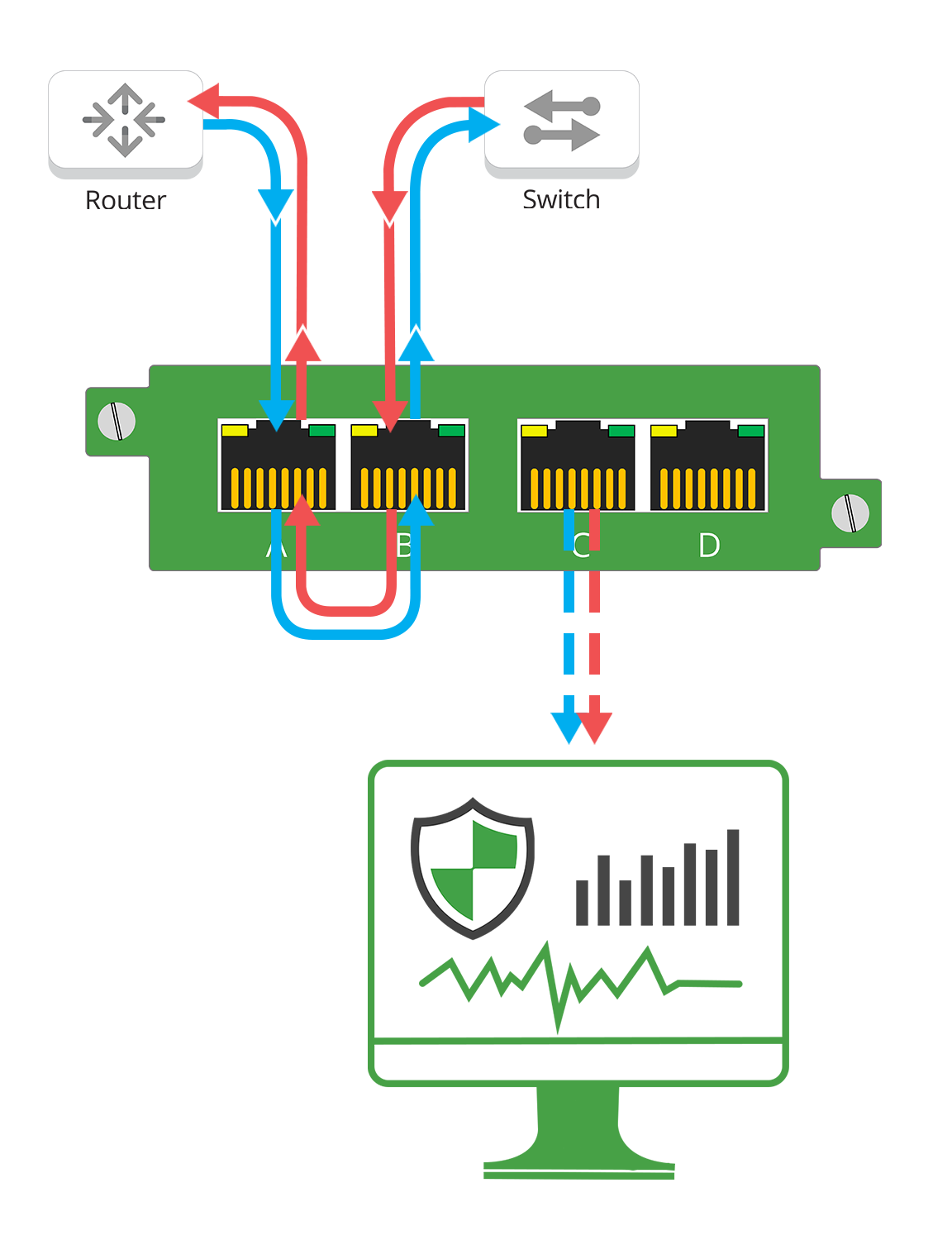
Keeping Clinical Systems Online: Why Packet-Level Network Visibility Matters in Hospital IT
Modern hospitals rely on complex digital ecosystems, making network reliability critical for uninterrupted patient care. Packet-level network visibility is essential for proactive troubleshooting,...