
Today’s critical infrastructure landscape makes up the fundamental building blocks of the connected world we live in. From the basic communication we enjoy through WiFi, internet and telephones to resources we may take for granted like energy, water, manufacturing, and transportation systems. Even our national security, such as The Department of Defense (DoD) and various Federal agencies, rely on similar operational technology (OT) environments. This critical infrastructure provides constant and reliable resources for our society, and it must be protected at all costs.
OT is the New Frontier for Cybersecurity Threats
According to Gartner’s OT Security Best Practices, “By 2021, 25% of asset-centric enterprises will adopt a hybrid model to secure operational technology (OT) environments with traditional security deployed alongside specialist OT security technology, up from 10% in 2018.”
In other words, the security challenges from the convergence of modern OT and IT environments and its goal to improve operations efficiency, performance and quality of services, is a growing threat. Pushing organizations across the industrial spectrum to re-evaluate their network visibility to address these challenges, is an important first step.
This vulnerability was illustrated recently in the Oldsmar, Florida water systems attack, where a hacker accessed the facility’s control system and was able to trigger an increase to the amount of lye in the water to dangerous levels. Driving home the reality that traditional firewalls and virtual private network (VPN) access sometimes leave systems exposed to outside intrusion.
How to Block Access from Reaching these Critical Systems
ICS environments face challenges to protect critical network segments from incoming threats through the very network infrastructure designed to protect them. Most OT and IT network environments send out-of-band Ethernet packet copies to security monitoring tools to analyze and respond to threats. Many visibility architectures or fabrics flow this out-of-band traffic from the separate facilities to a centralized or enterprise network for this analysis. These IT solutions and integrated systems, connect the network to the internet, indirectly exposing this once siloed infrastructure to outside vulnerabilities and threats.
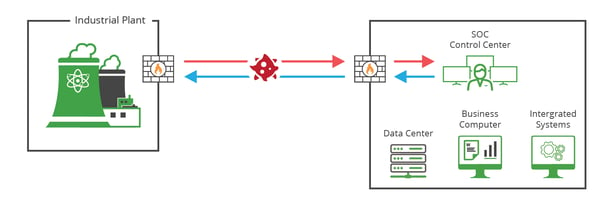 Diagram 1: A birds eye view of malicious activity being transmitted between different facilities or segments, exposing the network through bidirectional traffic.
Diagram 1: A birds eye view of malicious activity being transmitted between different facilities or segments, exposing the network through bidirectional traffic.
To address these challenges, a one-way data transfer between segments or facilities may be required. In addition to modern OT/IT security tools, such as firewalls, intrusion detection systems (IDS) and Security information and event management (SIEM), there is one piece of hardware that is quickly becoming a staple of ICS critical infrastructure — data diodes.
Unidirectional or one-way data flow in data diodes are designed to secure OT networks from external threats, eliminating inbound data flow and ultimately outside threats to OT network segments, while providing the needed out-of-band data flow needed to monitor.
Data Diode TAP technology is a more secure option for network visibility than SPAN ports from a network switch, where engineers will often connect directly to intrusion detection systems (IDS), or between segment facilities to monitoring tools. Not only can SPAN ports drop packets, hiding security vulnerabilities, but SPAN has bidirectional traffic, which opens back flow of traffic into the network, making the switch susceptible to hacking.
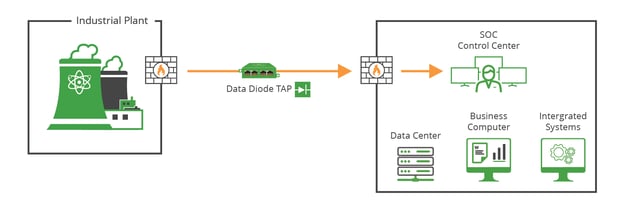 Diagram 2 illustrates how unidirectional traffic helps ensure monitoring traffic being transmitted from different facility segments remain secure.
Diagram 2 illustrates how unidirectional traffic helps ensure monitoring traffic being transmitted from different facility segments remain secure.
Data diodes can be found most commonly in high security environments, such as federal defense and Industrial IoT, where they serve as connections between two or more networks of differing security classifications. This technology can now be found at the industrial control level for such facilities as nuclear power plants, power generation and safety critical systems like railway networks.
How do Data Diode TAPs work?
Data diode TAPs are a purpose-built network hardware device that allows raw data to travel only in one direction. Data diode TAPs can be used as a traffic enforcer, guaranteeing information security or protection of critical digital systems, such as industrial control systems, from inbound cyber attacks.
A network TAP creates an exact copy of both sides of the traffic flow, continuously 24/7/365 and do not drop packets, introduce delay, or alter the data. They are either passive or “failsafe,” meaning traffic continues to flow between network devices if power is lost or a monitoring tool is removed, ensuring it isn’t a single point of failure.
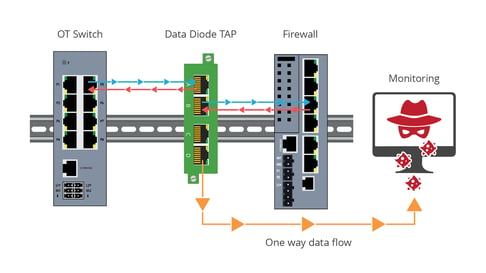 Diagram 3 illustrates how a data diode TAP is placed in a network segment, securing the traffic from the destination.
Diagram 3 illustrates how a data diode TAP is placed in a network segment, securing the traffic from the destination.
Data Diodes TAPs sit in a network segment between two appliances like a network switch and a firewall, that support the critical link. The Data Diode TAP sends a unidirectional copy of that traffic to the out-of-band monitoring destination, the link between the two appliances is unaffected. There is no physical connection between the Data Diode monitoring ports and the network ports, eliminating any possible intrusion from the destination.
These specifically designed TAPs physically do not send traffic back onto the network providing “no injection” tap visibility for 10/100/1000M networks. This hardware based one-way data transfer, ensures no Ethernet packets can physically be sent to the live Network TAP ports or SPAN ports. Did you know that Data Diode TAPs:
- Provide unidirectional traffic to protect against back flow of traffic into the network
- Provide 100% full duplex copies of network traffic
- Ensure no dropped packets, passing physical errors and support jumbo frames
- Are secure, do not have an IP address or MAC address, and cannot be hacked
The ultimate goal for Data Diode TAPs are to feed OT/IT security monitoring solutions “every bit, byte, and packet,” to ensure the network is properly analyzed and protected without introducing additional vulnerabilities from incoming traffic in the process. And that is why modern ICS security strategies are incorporating them alongside their network TAP and packet broker visibility fabrics.
Looking to add Data Diode TAP visibility, but not sure where to start? Join us for a brief network Design-IT consultation or demo. No obligation - it’s what we love to do.


