
A case for capturing all packets
With the recent Garland Technology and TOYOTech technical partnership, there will literally be no packets left behind in the network world. Garland’s line of Network TAPs provides complete packet visibility, from the simplest to the most complex network installations. Our parent company TOYO Corp built the first packet capture system capable of supporting rates of up to 100Gbps with no packet loss. This combined solution provides a robust solution for network professionals where packet analysis is the mantra.
Garland provides the medium for packets while TOYO offers the collection mechanism. See and Record every bit, every byte, and packet.®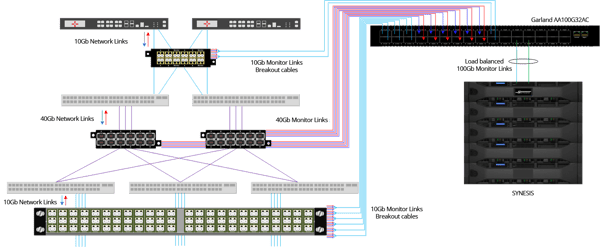
This is a proven partnership by TOYO in APAC. Being part of the Garland ecosystem provides immediate key benefits to our respective customers and channel partners:
- Lower cost and less manpower required since both Garland TAPs and SYNESIS are easy to deploy
- Lossless packet capture provides confidence that data collected is complete
- Lower CAPEX and OPEX. Instead of multiple units, an all-in-one capture system can record aggregated traffic up to 100Gbps
- Synchronized timing during data collection making troubleshooting much easier
Case Study: Hardware hack during manufacturing compromises commercial & national security
On October 4, 2018, Bloomberg Businessweek revisited a hardware hack that had long lasting ramifications for our national security and the trust between an appliance server vendor and its customers. This “hack” affected the world’s biggest companies and triggered the beginning of the end of one major server supplier. More recently, subsequent articles suggest not all parties are in agreement of the findings and ramifications, and the vendors and targeted companies are demanding that the article be retracted. So, a dilemma. Who are we to believe? From a network engineering perspective, we need to practice due diligence and perform our own research.

Although the jury is still out on whether the original article is totally factual, it did bring to light how a major server vendor may have been infiltrated by a hacking arm of a certain government. The vendor’s servers were highly regarded in the industry. They were purchased and deployed in large numbers by well-known high-tech companies needing video compression for media intensive applications. Through sleuth and deception, a “grain-of-rice” sized electronic component was amended into the vendor’s numerous motherboard designs. This component was programmed to push malicious code into host server’s circuitry and then send inconspicuous pings to rogue servers for further instruction. Not until a few of the customers performed their due diligence with detailed hardware security analysis did the problem surface. Findings were reviewed internally and also shared with the US government. From there you can imagine the events that followed. Accusations were made followed recently by denials. It affected not just how companies deployed and evaluate new technology from any vendor but caused mistrust between vendor and clients.
“Packets don’t lie”
- anonymous old school network engineer
How can a network engineer prove or disprove the breach? Let’s start with the simple traffic characteristic – low number of pings from the server to unknown destinations. The traffic rates generated were so low that they were deemed anomalies and not worth the investigative effort. A TopN monitoring tool that list bandwidth hogs would not have registered or made it visible at all. However, a solution that provided full packet visibility and capture capacity would have recorded all traffic, which would then be made available for detailed investigation.
Even if an IDS/IPS is in place but is configured to only record suspect traffic, the data would have been missed. With a Garland installation, all traffic being sent to an IDS/IPS may be mirrored automatically to a network recorder like SYNESIS. Unlike the IDS/IPS, the SYNESIS would record all traffic which can then be made available and investigated in detail. Packets provide the most detailed documentation that can prove or disprove the event ever happened.
Sometimes, you don’t know what you don’t know. Your company’s reputation may even hang in the balance based on the findings Garland and SYNESIS is a powerful, unique solution that allows teams to fully investigate what they don’t know. Every bit, byte, and packet® is seen and recorded leaving nothing to chance.
[Want to learn the benefits of TAP vs SPAN? Check out our white paper TAP vs SPAN: Real Network Visualization.]
