
It wasn’t too long ago that IT security teams were talking about achieving 20% encrypted traffic.
But encryption efforts are quickly gaining traction. Mozilla research found the average volume of encrypted web traffic finally surpassed the volume of unencrypted traffic.
To the general public, this shift is proof of a transition to safer, more private internet experiences. However, the security community knows that encrypted traffic has other implications for corporate data protection.
Encrypted traffic can be beneficial for network security, but only if you take the right approach to monitoring.
Encrypted Traffic Is Difficult to Analyze
Generally speaking, your existing security tools won’t be able to monitor encrypted traffic. SSL encryption certainly improves data privacy on the end-user side, but it blocks the packet visibility security tools rely on to keep your business network safe.
The problem will only grow as more and more traffic is encrypted. Unfortunately, your problems with encrypted traffic don’t stop at volume alone.
As we’ve seen so many times, attackers are sophisticated enough and detailed enough to pinpoint weaknesses in your network—and the encryption blind spot is no exception.
>> Download now: IT Security [Whitepaper]
Attackers have increasingly used SSL as a way to mask malware and other threats on their way into your network. Whether they’re infecting your network, stealing data, or making a foothold for callback communications, encrypted traffic can be the perfect way to bypass your security solutions.
One security company has said that its platform blocks nearly 10 million SSL/TLS-related threats per day. And because your security solutions alone aren’t enough to monitor encrypted traffic, it’s only a matter of time before a threat sneaks through.
The only way to stop attacks like encrypted SSL floods, SSL renegotiations, and encrypted web app attacks is to ensure you’re monitoring each packet of encrypted traffic. This may seem easier said than done, but it doesn’t have to be.
How to Monitor Your Encrypted Traffic
The only way to guarantee visibility of encrypted traffic for your security tools is to decrypt the traffic before analyzing. Once the data is decrypted, it can be sent through your firewall, intrusion prevention system, denial of service tool, or any other security application.
After you’ve inspected the decrypted traffic for malware or threats, you can re-encrypt it to maintain security.
That’s the basic idea, but how do you actually execute? We have two scenarios to give you a better idea of how this would look in a real-world deployment.
In this first scenario, you have encrypted traffic coming in from a router and you want to pass it through to both an IPS and a firewall.
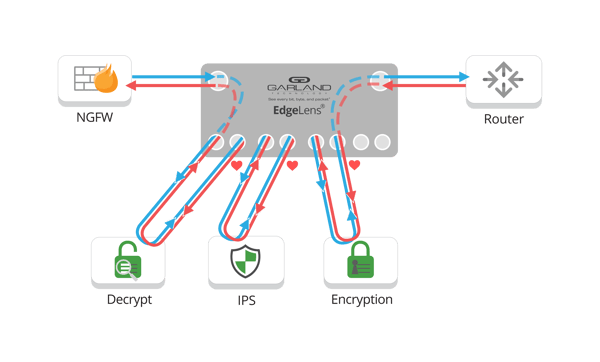 Here, you see that the traffic is first sent through a decryption solution like A10 Network's Thunder® SSLi. The decrypted data is analyzed by the IPS, re-encrypted by the A10 solution, and finally analyzed by the firewall.
Here, you see that the traffic is first sent through a decryption solution like A10 Network's Thunder® SSLi. The decrypted data is analyzed by the IPS, re-encrypted by the A10 solution, and finally analyzed by the firewall.
This scenario can be played out in either a passive deployment or active in-line deployment where you can leverage the bypass features of Garland network TAPs to troubleshoot when necessary.
The second scenario involves Garland’s EdgeLens® or Modular Chassis solution with a Next-Generation Firewall from our technology partner, Palo Alto Networks, along with a variety of other security tools.
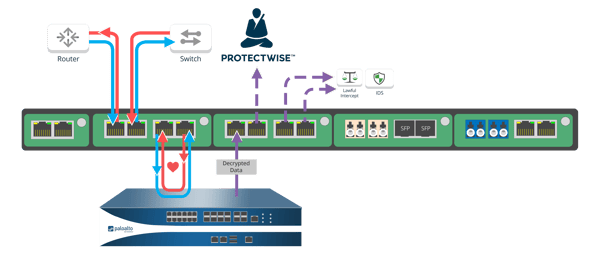
In this case, the EdgeLens or modular chassis is monitoring all traffic sent between a switch and router (encrypted or unencrypted). EdgeLens can identify and select encrypted traffic and route to Palo Alto’s NGFW, which has decryption capabilities built in.
In addition to decrypting data, the NGFW can make a copy of the decrypted traffic and EdgeLens can then replicate to any number of other monitoring tools, including Protectwise's Grid.
Choosing between these two use cases will depend on your specific network architecture and situational demands.
Looking to add inline or out-of-band security solutions, but not sure where to start? Join us for a brief network Design-IT consultation or demo. No obligation - it’s what we love to do.

