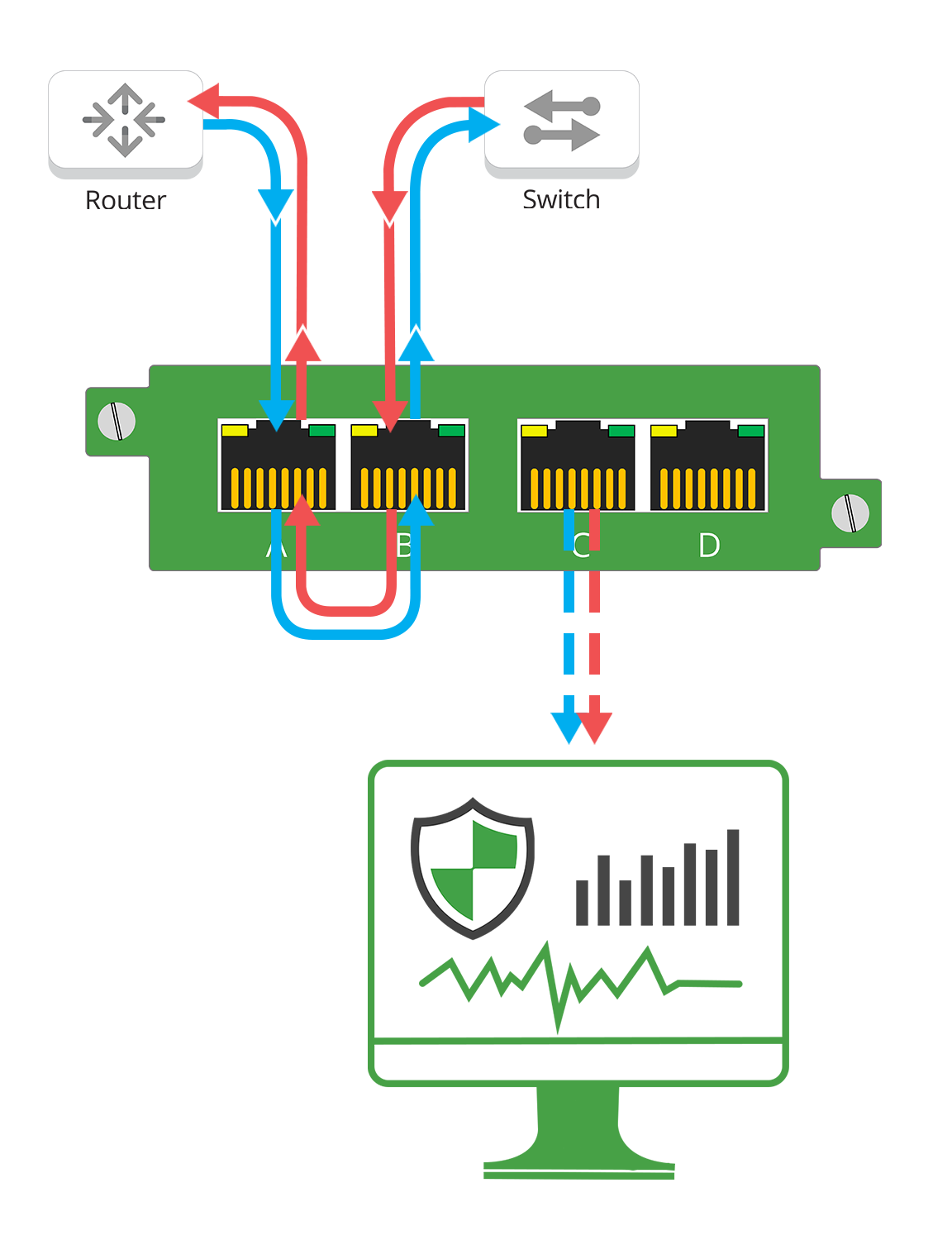
Secure Networks Ep 36 - The Packet Forensics Files
This week, our very own Neil Wilkins got to talk “security at scale” with Michael Morris from Endace. They discussed the importance of planning for growth, proper security training, and working to...