
Despite ever-increasing cybersecurity budgets, attackers continue to find ways around network defenses and are on track to cause over $6 trillion in damages annually by 2021. As cloud adoption continues to grow, attackers are taking advantage of new threat vectors and 84% of organizations say traditional security solutions don’t work against them.
This is especially problematic in the industrial sector where cyber attacks aren’t just costly—they can be a matter of life and death. Ignoring cloud computing isn’t an option. The advantages of moving industrial processes to the cloud are just too beneficial to ignore.
Cloud environments and industrial networks need an additional layer of security to address vulnerabilities without sacrificing the cost efficiency, scalability, and flexibility of a modern architecture. Air gapping is the answer to this challenge.
Introduction to Air Gapping
The best way to avoid a cyber attack is to keep your devices off the Internet altogether. That’s what air gapping aims to do. By physically isolating devices and applications from outside networks, you ensure that when an attacker penetrates your defenses, they aren’t able to move laterally and compromise key components of your IT/OT infrastructure.
When devices in an air-gapped network are stripped of any wired or wireless network interface to the outside world, you’re sacrificing modern connectivity for maximum privacy and security. Unlike in today’s typical networks, devices in an air-gapped network must transfer data physically. Data transfers are usually performed with USB connectivity or removable disks to keep devices isolated from network vulnerabilities.
In theory, you might think that air gapping every device on an industrial network might be the answer to security problems. However, performance demands and the rise of innovative Industry 4.0 use cases for IoT devices, artificial intelligence, machine learning, and other technologies have made air-gapped networks seem too limited.
Not only that, but sophisticated attackers have already proven that air-gapped networks aren’t entirely invulnerable to threats. A few threats that have targeted air-gapped networks in the past include:
- Stuxnet: This malware famously disrupted Iran’s nuclear facilities by infecting the air-gapped network via a compromised thumb drive.
- AirHopper: Researchers created this proof of concept malware that could demonstrate data exfiltration from air-gapped devices. It used an infected graphics card on the air-gapped device to send electromagnetic signals to nearby phones that captured data.
- BitWhisper: Researchers created an attack method that created a “covert bi-directional communication channel between two nearby air-gapped computers communicating via heat. The method allows bridging the air-gap between the two physically adjacent and compromised computers using their heat emissions and built-in thermal sensors to communicate.”
These are just a few of the ways that attackers and researchers have proven that air gapping isn’t a fool-proof measure for protecting key assets and applications. But that doesn’t mean that it’s not a worthwhile security measure for cloud and industrial environments.
Rather, the key to getting the most out of air gapping to secure cloud and industrial environments is being able to maintain visibility of all traffic and communication—not just within internet-connected networks, but within air-gapped ones, too.
>> Download now: Cloud Visibility [Free Whitepaper]
Maximizing Visibility into Air-Gapped Networks
Skeptics will say that air gapping is no longer a viable security tactic because of the widespread connectivity of industrial networking components. Increased connectivity combined with ever-growing usage of cloud-based solutions have pushed industrial network architects to look for more modern answers to cybersecurity issues.
But the reality is that air gapping continues to provide an additional layer of security even in cloud-based environments. The only difference is that we’ve gone from air gapping as a “set it and forget it” tactic to one that must be monitored closely.
This speaks to the larger challenge that industrial network architects face. When you start to deploy public and private cloud environments, how are you able to maintain visibility of all packets coming into and going out of the network in a way that keeps you in complete control of security? Designing industrial networks with passive network TAPs and the right network packet brokers has always been important. But new cloud environments and air-gapped networks require a more dedicated solution.
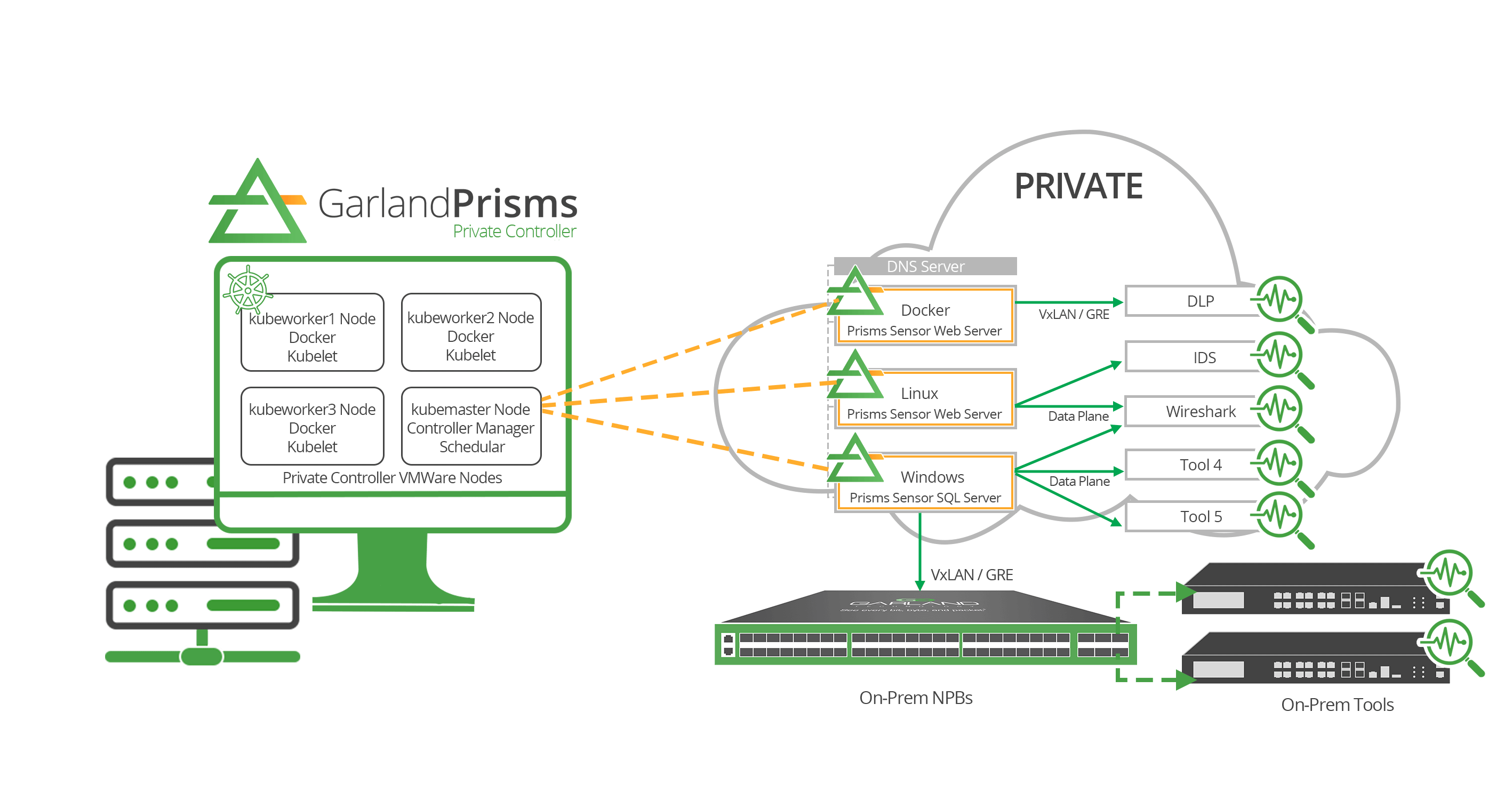
With the born-in-the-cloud Garland Prisms solution, you get a 100% out-of-band and passive platform that works with any cloud, supports all monitoring tools and systems, and is capable of performing any kind of cloud traffic mirroring. This is a cloud TAP solution that guarantees all packets are delivered to the proper monitoring tools and services. To extend these capabilities to air-gapped networks, Garland Prisms introduces on-premises management options that will help industrial environments remain secure without sacrificing cloud capabilities.
You already know that your industrial environment comes with different networking and security requirements than typical IT networks. You use all kinds of accessories like DIN Rails Mounting Kits, Field DC-DC Converters, and Screw Power Locks to meet unique cabling and environmental demands. If you’re leveraging air-gapped networks to increase security, a dedicated cloud visibility solution should be viewed as another essential network accessory.
There’s an opportunity to balance the benefits of cloud environments with the air gapping needs of industrial networks.
Looking to add a virtual visibility solution to your industrial deployment, but not sure where to start? Join us for a brief network Design-IT consultation or demo. No obligation - it’s what we love to do.

